I have been going through some security reviews with some third party security specialists. As part of that work, they have come back with some standard recommendations of the default Microsoft Azure AD settings that you should review and consider changing to improve your environments security.
Before we start just a word of warning. Make sure you fully understand the impact of any changes you are making
Table of Contents
- Enable Continuous Access Evaluation
- Require MFA to Join a Device to Azure AD
- Configure Directory Level Timeout
- Block Non-admins Browsing the Azure AD Administration Portal
- Block Non-admin from Registering Enterprise Applications
Enable Continuous Access Evaluation
Assuming you are using Conditional Access (and you really should be). Continuous access evaluation is currently a feature in preview (at the time of writing), but it is recommended to enable it now or check you have it on.
Without the feature enabled users security tokens expire after an hour. It is only then that rules such as their Conditional Access rules are reevaluated. But it could be the user’s device has moved to a different IP address or the user’s account has been disabled. Without Continuous access evaluation, there can be a lag resulting in users retaining access when they shouldn’t
Microsoft lists the key benefits
- User termination or password change/reset: User session revocation will be enforced in near real time.
- Network location change: Conditional Access location policies will be enforced in near real time.
- Token export to a machine outside of a trusted network can be prevented with Conditional Access location policies.
Read more here: https://docs.microsoft.com/en-us/azure/active-directory/conditional-access/concept-continuous-access-evaluation
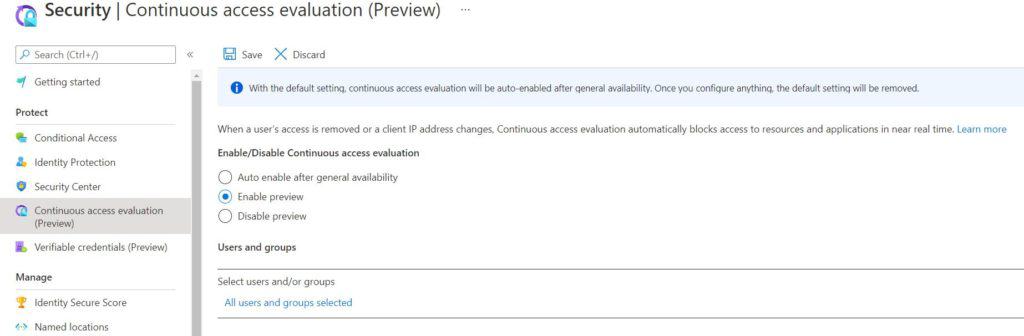
How to enable
- Logon to you AAD admin portal https://portal.azure.com/#blade/Microsoft_AAD_IAM
- Under Manage click Security
- Under Protect click Continuous access evaluation
- Enable and Save – If required you can just apply to a group to evaluate first
Require MFA to Join a Device to Azure AD
By default, any user with an active account can join a device to Azure AD and they don’t even need MFA. The risk here being if a users account has compromised an attacker could join a computer to your Azure AD and potentially get further than we would like.
In addition to requiring MFA to join a device to Azure AD, I would also recommend you limit the accounts that can join computers.
Setting who can join devices
- Logon to you AAD admin portal https://portal.azure.com/#blade/Microsoft_AAD_IAM
- Under Manage click Devices
- Click Device Settings
- Under “Users may join devices to Azure AD” click Selected and use the “No member selected” link below to select a user or group gor who should be allowed.
- Click Save at the top
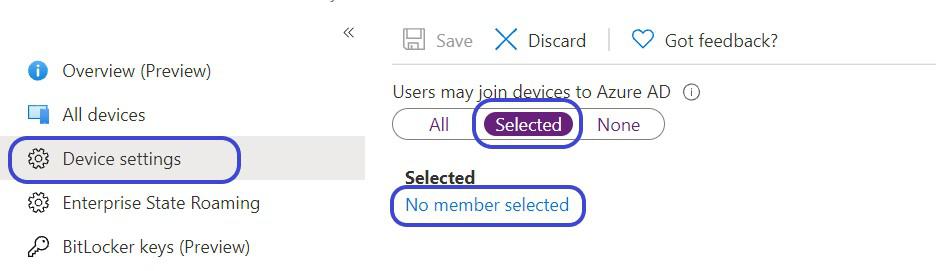
Enforcing that MFA is required to join a device
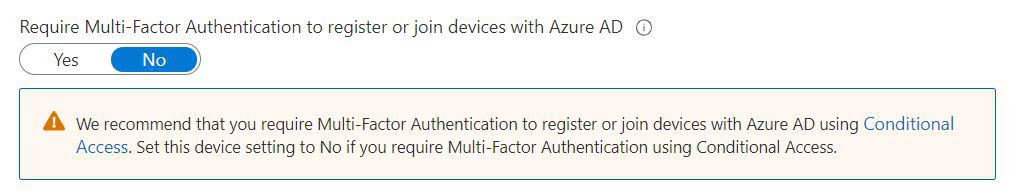
So under Device Setting where we were in the previous section, there is actually an option “Require Multi-Factor Authentication to register or join devices with Azure AD”. However, Microsoft now recommends you don’t use that and instead create a conditional access rule.
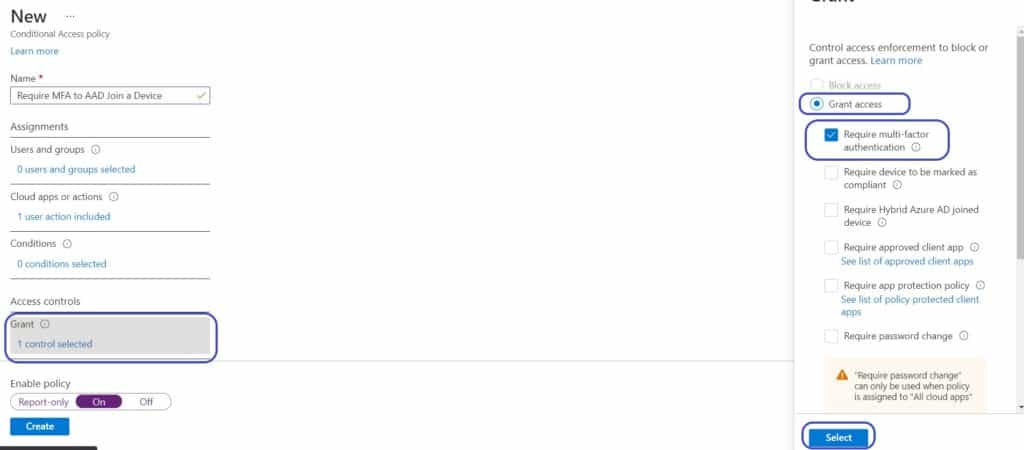
To create a Conditional Access rule to require MFA to join a device,
- Logon to you AAD admin portal https://portal.azure.com/#blade/Microsoft_AAD_IAM
- Make sure the above mentioned “Require Multi-Factor Authentication to register or join devices with Azure AD” settings is set to No and Save
- Back at the Azure AD blade. Under Manage click Security
- Under Protect click Conditional Access
- Create a New policy
- Name: <set a name that matches your standard>
- In the “Cloud apps or actions” section
- Set what this policy applies to: User Actions
- Select the action this policy will apply to: Register or Join Devices
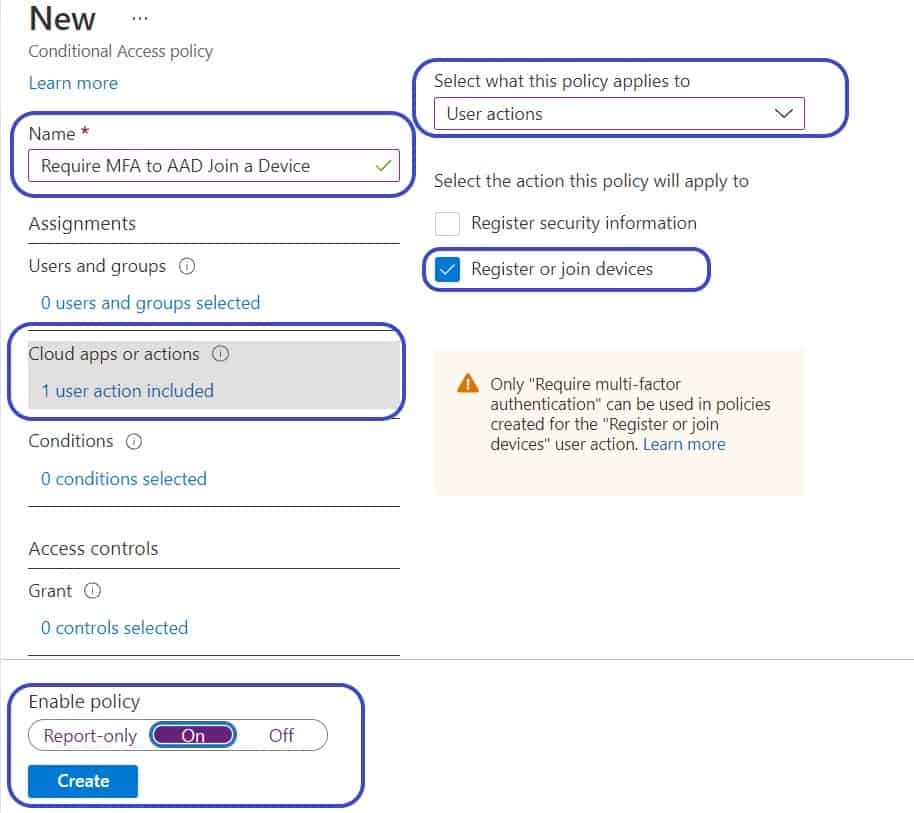
- In the Grant section
- Select “Grant access” and “Require multi-factor authentication”
- Click Select
- Set the Policy as On
- Click Create
Configure Directory Level Timeout
The directory level timeout will log out admins after a definable amount of idle time. This will prevent the admin from being able to leave the admin portal open idle. Especially important if the computer has no Windows level idle timeouts.
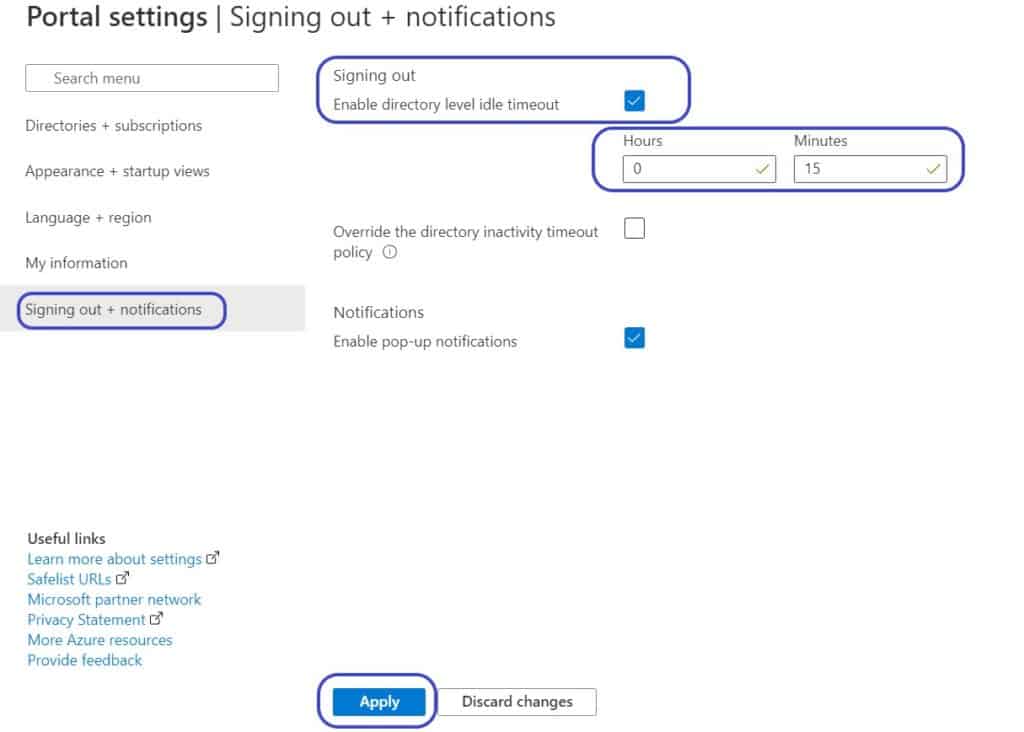
How to enable
- Logon to the admin portal as a global admin https://portal.azure.com/
- Click the settings icon in the top-right
- On the left select Signing out + notifications
- Tick “Enable directory level idle timeout” and set the idle timeout as required
- Click Apply
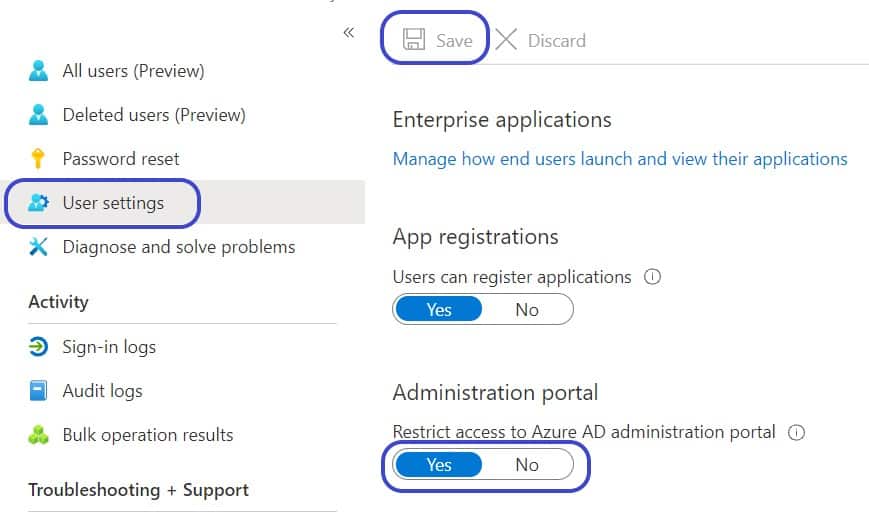
Block Non-admins Browsing the Azure AD Administration Portal
By default, non-admins will have access to read and browse the AAD admin portal. To disable this,
- Logon to you AAD admin portal https://portal.azure.com/#blade/Microsoft_AAD_IAM
- Under Manage click Users
- Click User Settings
- Set “Restrict access to Azure AD administration portal” to Yes
- Click Save at the top
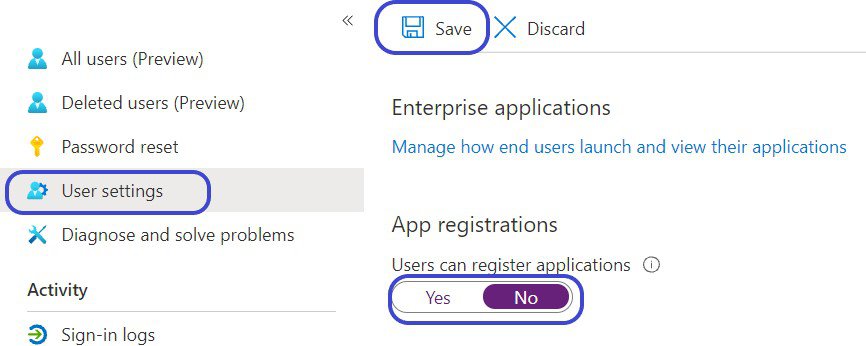
Block Non-admin from Registering Enterprise Applications
In most circumstances, you wouldn’t want users to be able to register custom AAD Enterprise Applications. To disable non-admin being able to register applications,
- Logon to you AAD admin portal https://portal.azure.com/#blade/Microsoft_AAD_IAM
- Under Manage click Users
- Click User Settings
- Set “Users can register applications” to No
- Click Save at the top