In this post I will show how you can enabled Windows Bitlocker encryption from a command prompt using manage-bde. The full Microsoft documentation for manage-bde can he found here https://docs.microsoft.com/en-us/windows-server/administration/windows-commands/manage-bde
System Drive C:
- Open and admin command prompt
- Enter the command
manage-bde -protectors -add C: -rp
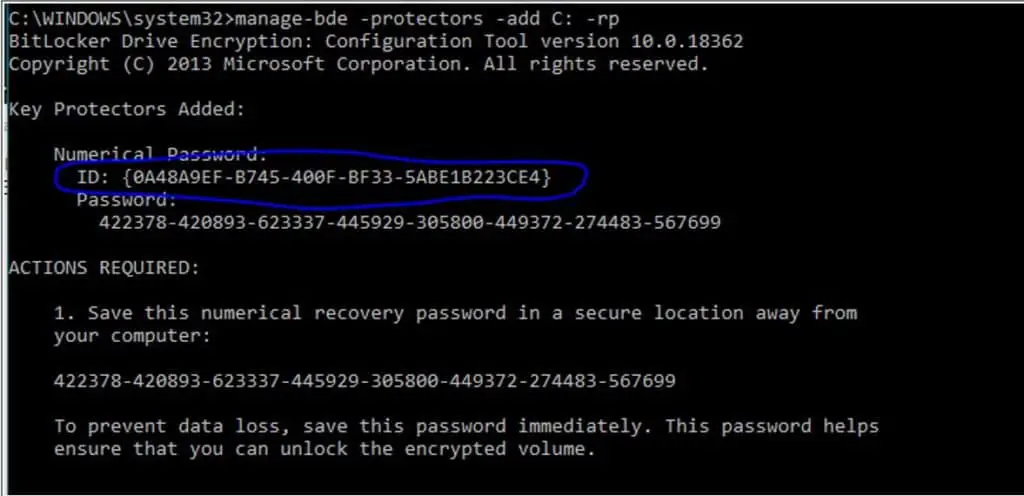
- Optional step but recommended – To backup the recovery password to Active Directory. Make sure you can ping one of your Domain Controllers and issue the below command. Replacing the ID with your own, presented after adding a protector in the previous step. If you are not backing up to AD I recommend you take a manual backup of the password and the longer GUID at the bottom of the prompt.
manage-bde -protectors -adbackup C: -id {0A48A9EF-B745-400F-BF33-5ABE1B223CE4}
- Finally enter the below command to switch Bitlocker on, then reboot
manage-bde -on C:
Additional drive(s)
For any additional drives i.e a D: drive you would follow the same steps as above replacing C: with your drive letter. We also will want to run an additional command -autounlock so no manual action is required to unlock the drive when needed.
There is no need to reboot after the last command
manage-bde -protectors -add D: -rp
manage-bde -protectors -adbackup D: -id {B558C629-E5EA-4C74-BBBC-84D491A28134}
manage-bde -autounlock -enable D:
manage-bde -on D:
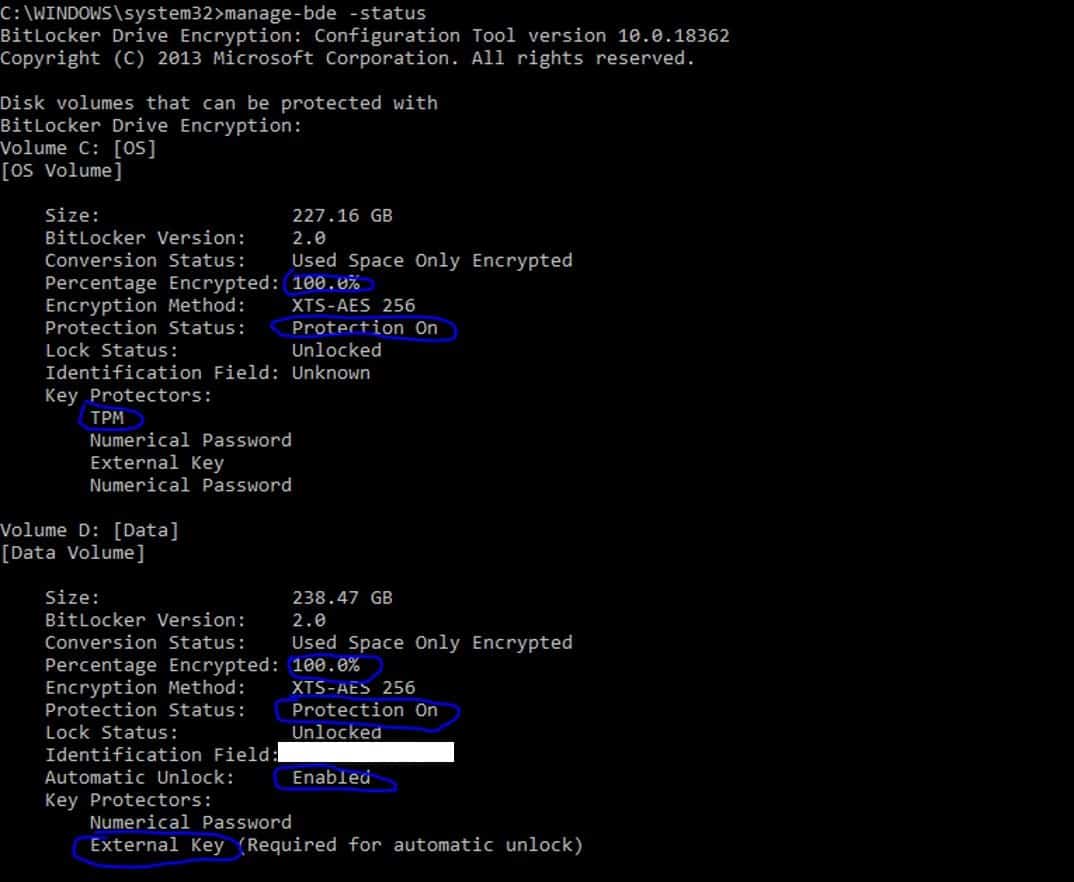
Checking the status
You can use -status to check everything is as it should be
manage-bde -status
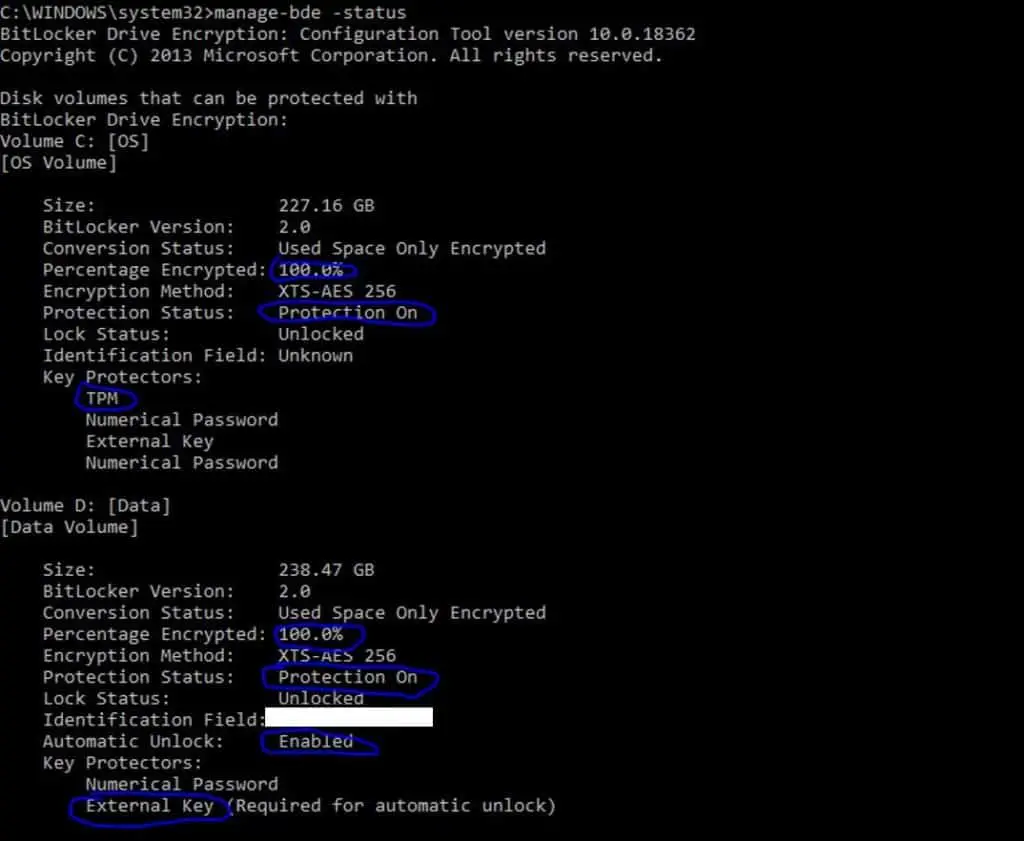
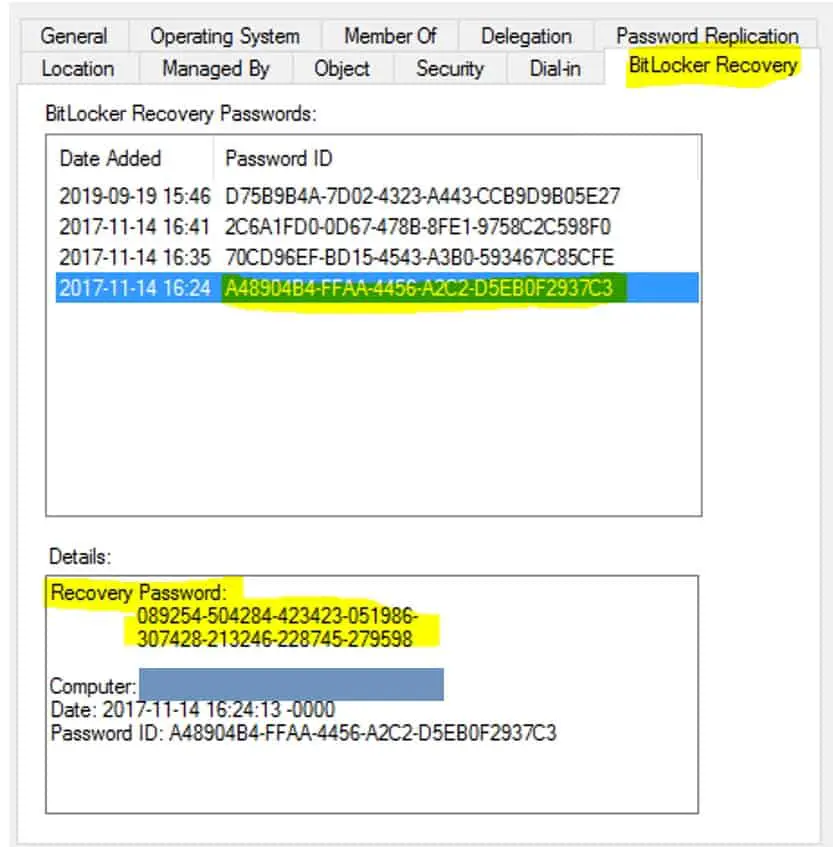
Checking the backup status in Active Directory
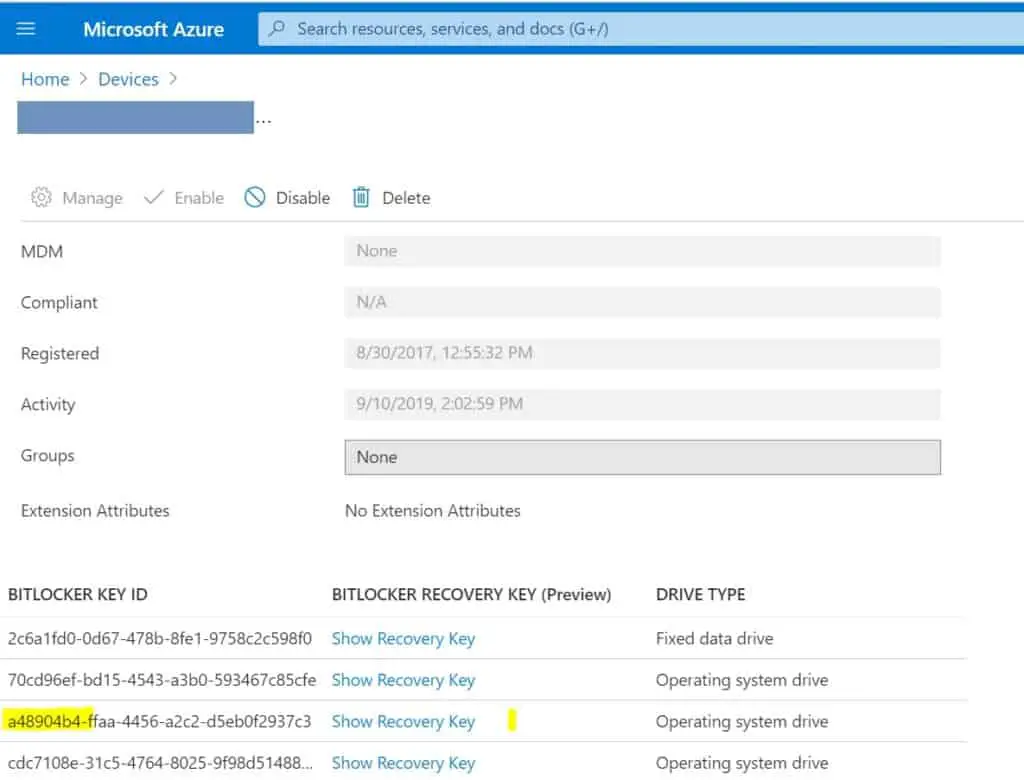
Checking the backup status in Azure AD (if applicable)
Can be found after searching and selecting the computer in the devices section.
“Replacing the ID with your own”
How do I determine the ID? For example, is it an objectGUID in AD? Is it some other GUID?
Hi,
This refers to the ID previously generated by manage-bde -protectors -add C: -rp command
Take a look in the screenshot just above that paragraph, the ID is circled in blue
Let me know if you need any more information
Phil