Recently I was experimenting with the new Azure AD Condition Access Device Filters, but I wasn’t getting the results I was expecting.
In my tests, I had created a Conditional Access rule to block a user from being able to sign in from any devices except a device id I had added into my filter. This worked fine if the user used the Teams application or Edge. But if they used Chrome to access Outlook Web, the filter would not match and the sign-in was blocked.
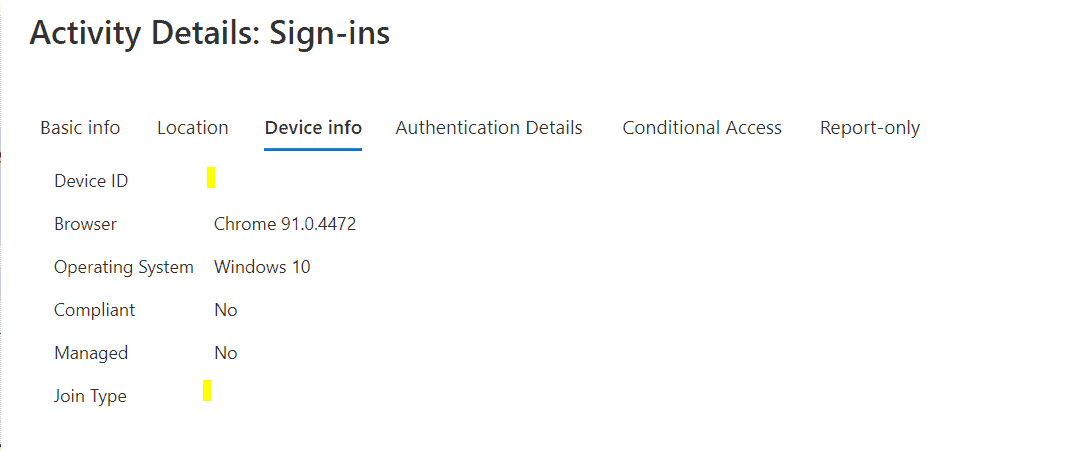
It turned out that when using Chrome the browser was not passing the Device ID as part of the sign-in process. In the Azure AD Sign-in log, I would see on the “Device Info” tab that the “Device ID” and “Join Type” fields would be blank, as you see in the above image. If the user used Teams or Edge the fields would be completed so my device filter for the Device ID would work.
The solution in my case was to push out the Chrome extension Windows 10 Accounts
Use this extension to sign in to supported websites with accounts on Windows 10. If you have a Microsoft supported identity on Windows 10, you won’t be required to enter your credentials to sign in to supported websites. You’ll need to use this extension if your organization has implemented conditional access policy. Currently, this extension supports Azure Active Directory identities.
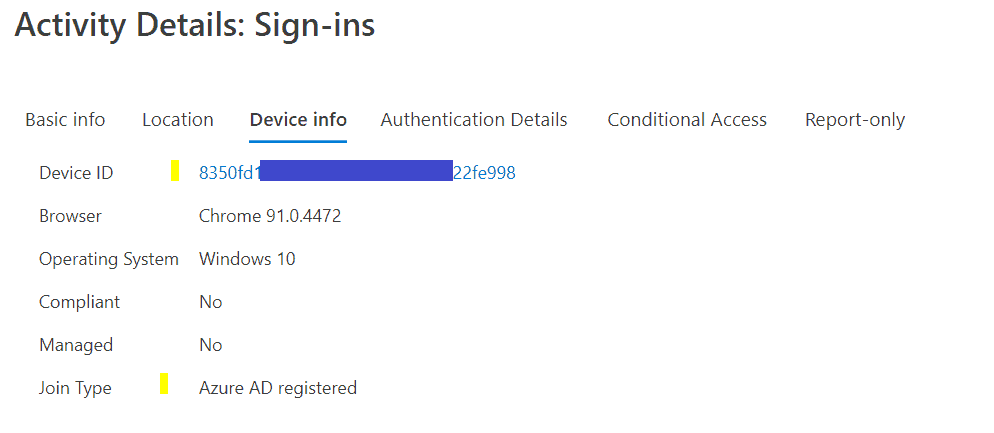
After the extension was installed Chrome clients would pass the Device ID during the sign-in process
How to silently deploy the Windows 10 Accounts Chrome extension
Check out this post Chrome – Silently Deploying an Extension using the Registry